The good, the bad and the ugly
It’s seriously hard to believe that in the year 2022, Internet scams still exist. It’s even harder to believe, that we, the public still fall for them. But they do exist, and we do fall for them. Every. Single. Day.
In fact, the internet is rampant with consumer cybercrimes. And it isn’t showing signs of dissipating anytime soon. If anything, it’s on the rise.
We’ve put together a quick list of the top three social engineering scams circulating cyberspace, as we speak, and a bunch of other data on recent consumer cyber scams, to help you, Jo public, stay clued up and plugged in, so that you can avoid falling for any of these yourself, this year, or any time soon.
Check them out:
1. Google Voice Scam
Google what? Here’s how it works.
The scam: How many times have you ever posted something online? Millions, right? Say you want to sell something or ask for a recommendation for a service and innocently leave your phone number in the post. In this scam, the fraudster will contact you, say they are interested in whatever it is you asked for, BUT, say that they want to verify first that you aren’t a scammer. (Cheeky). They’ll tell you that you are about to get a verification code from Google Voice (their virtual phone and text service) sent to you, and ask you, to read it back to them.
Sounds innocent enough, right? Wrong. What they are actually doing is setting up a Google Voice account in your (!) name. They then steal your identity via your voice and go on to carry out further scams by pretending to be you and in the interim, hiding their true identity from the law.
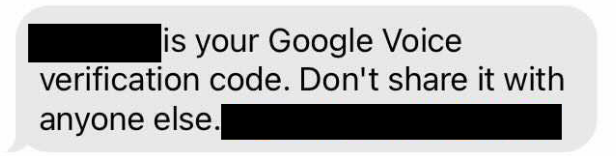
The lesson: “Never, never EVER share verification codes with anyone. And if it’s already too late – worry not, you can find out how to reclaim your account at the Google Voice Help Center.
2. Fake-Job Frauds
The scam: Looking for a job? We’ve all been there. Posted your contact info and personal details on legit job websites? Sure you have. Scammers know this and harvest contact info and personal details from résumés, pretend to be recruiters and then call, email, text or reach out to you on social media with high-salary or fake work at home jobs. Why? For a variety of reasons. Sometimes to get additional info about you; other times, to convince you to send money for bogus home-office setups or fake fees. Scary, but true.
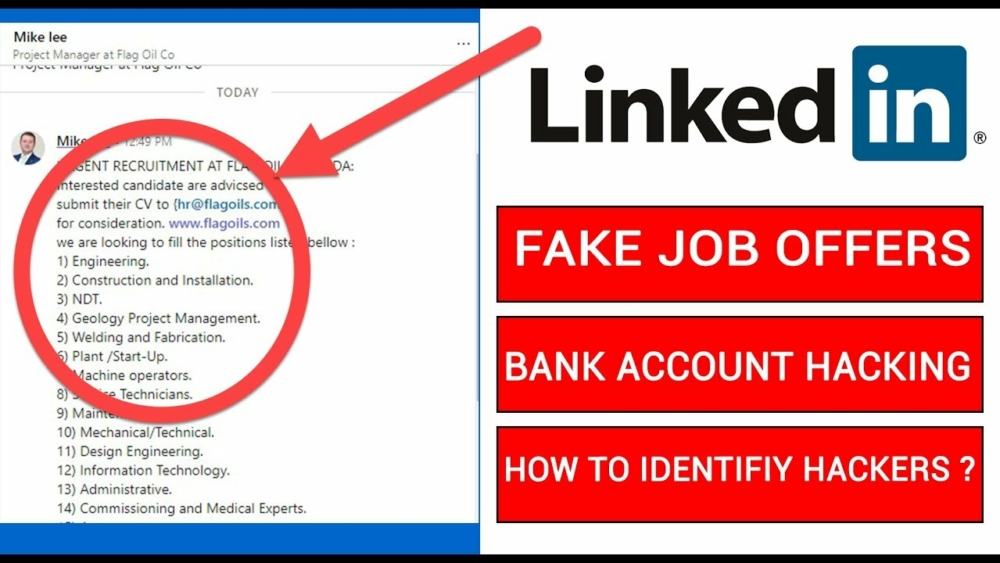
The lesson: Always set up a separate email address just for job hunting. Also, take care to set up a free Google Voice phone number that rings on your phone, but keeps your real number private. And, if you do get potentially lucky and get yourself a sudden job offer, first call the company’s HR department to verify its real. These small steps could be the difference between potential work and … becoming the unsuspecting victim of fraud. Yikes!
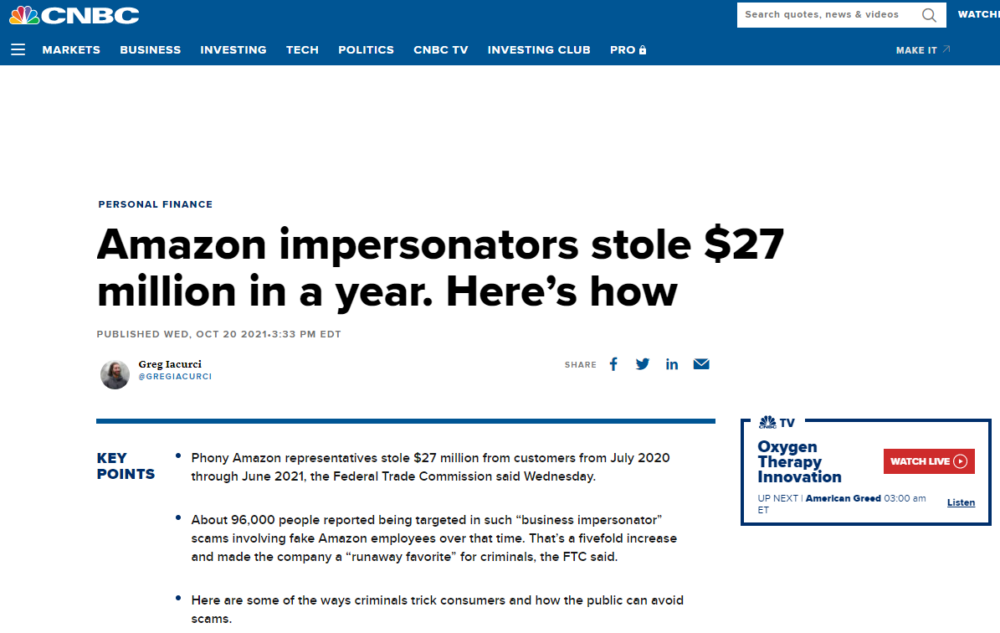
3. Fake Amazon Employees
The scam: Everyone knows, loves, and totally trusts Amazon. Right? Especially since Covid, we’ve all been there at 2am ordering away like nobody’s business. However, it’s important to know that one-third of business-impostor fraud complaints involve online scammers pretending they work for Amazon. Last year alone, fraudsters stole a whopping 27 million! Think you’d never fall for this? Think again. The Federal Trade Commission (FTC) reports that
“Older adults are four times more likely to lose money and get hit harder — losing a median of $1,500, versus $814 for younger adults — in such scams. Why? Because Amazon is the biggest, best-known company in the online sales space,” which makes it so credible, few would question it.
The lesson: If you get a call, a text, email and/or a social media message about suspicious account activity, raffles, or unauthorized purchases… IGNORE it! And if you think you may have a real account problem, just contact Amazon customer support at 888-280-4331 to check it out.
Now that we’ve covered those general scams, lets look a little into the psychology of scammers.
Internet scammers are nothing if not highly adaptable and opportunistic. They know how to look at what’s going on in the world and take advantage of any current situation, no matter how good or bad, in order to put a few extra coins in their pockets.
Scams and the War between Russia and the Ukraine
Take the Ukraine/Russia situation for example. Jakub Kroustek, Avast Malware Research Director said that:
“We often see parallels between what’s happening in the real world and the threat landscape when it comes to how threats are being spread and their targets. In Q1/2022 we saw a significant increase in attacks of particular malware types in countries involved in the war. Compared to Q4/2021, we saw a more than 50% increase in the amount of remote access trojan (RAT) attacks and more than 20% increase in information stealer malware attacks we blocked in Ukraine, Russia, and Belarus, which could be used for information gathering or espionage,”. You can read more about that case, here.
So, we’ve discussed opportunism, but what about ye old chestnuts of cybercrime? We are of course referring to EMOTET, one of the most long lasting and difficult fraud nuts to crack, Like, ever.
EMOTET, a legend in cybercrime
EMOTET is one of the most professional and long-lasting cybercrime services out there. We are talking serious Malware. It was first discovered as a banking Trojan in 2014, which then evolved into the go-to solution for cybercriminals over the years. Why? Because the EMOTET infrastructure was the perfect door opener for computer systems on a global scale. Primarily using Word docs to get into people’s computers and their lives, once unauthorized access was successfully established, it was then sold to other top-level criminal groups to deploy further illicit activities such data theft and extortion through ransomware. And the list goes on. You can read more about this genius cybercrime scam and its eventual downfall, here.
So, we can conclude from the information available that cyber scams are RIFE and growing. However, up until today, most of the news has only covered the effect that cybercrime has on enterprises and large organizations, but today, the numbers undoubtedly show that:
In 2022, consumers will be affected more than ever before
by cyber threats.
Consumers: A growing target
Cybercriminals as we have mentioned, are smart. Seriously smart. Today, they are using everything they’ve learned from attacking enterprises and are employing those skills to attack the consumer. Unfortunately, most consumers are completely unaware that they are likely to be a target in many scenarios. For example:
Ever thought you could get hacked by downloading a movie? Crazy right? Think again. A crypto miner was recently discovered by researchers piggybacking off of a torrent download of Spider-Man: No Way Home. The miner evades endpoint protection products and adds exclusions to Windows Defender Antivirus. It also creates persistence and spawns a watchdog process to maintain its activity. This type of advanced threat puts global mases of people at great risk. You can read more about this threat and others like it here.
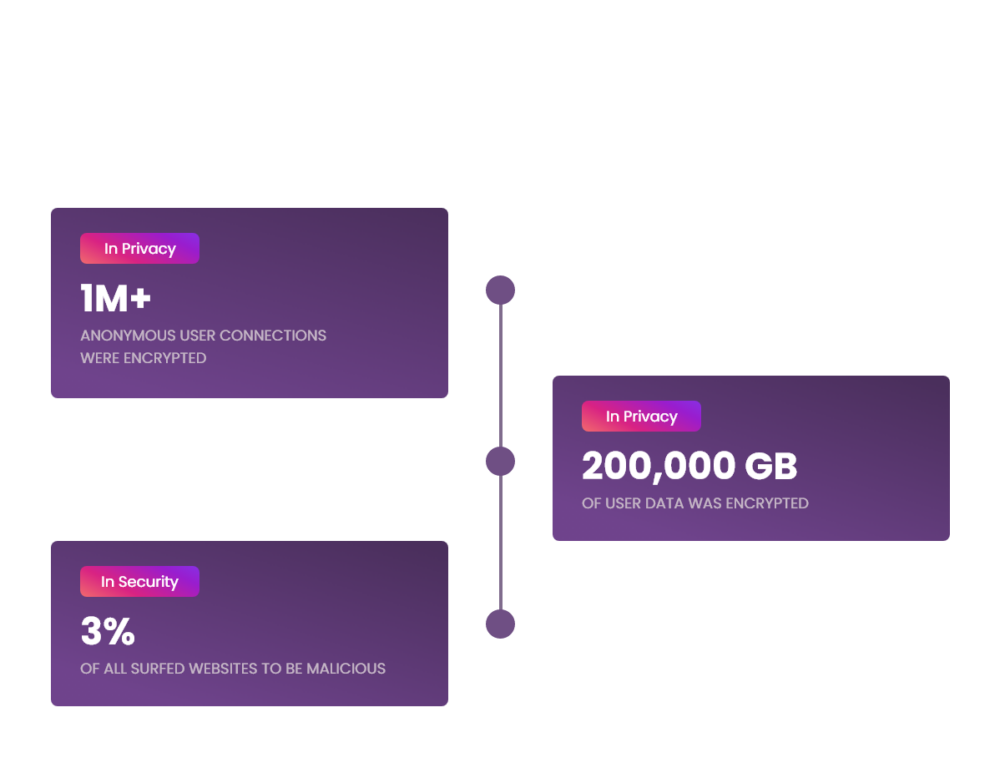
Consumer Cyber Security and Privacy Stats: The numbers speak for themselves
In a nutshell
It’s safe to say that its clear as day that cyberattacks are no longer just a threat to enterprises. Every John Doe is now a target. Thing is, it’s our collective duty, as consumers, to help win the war against consumer cybercrimes by staying up to date on what’s happening and making it our business to gain the tools to prevent those scams, before they take off globally, and millions are lost.
That’s why we’ve taken it upon ourselves as experts in the cyber security field to keep you, our readers, in the know of every scam as it happens, so that together, we can help slay the cyber scammer and save a whole lot of green, in the process.
Stay tuned and watch this space for more vital info on consumer cyber scams!